You might be wondering why you’d need to setup CA trust in your vSphere Supervisor. Certainly, in earlier versions it perhaps wasn’t necessary. With the addition of several services that can be deployed into the Supervisor though, having it be able to trust your own certificate authority (CA) starts to become desirable. And if you have the sort of environment that doesn’t have a direct line to the internet, it’s actually necessary.
Airgapped environments, for example, can’t pull anything directly from the internet. Any files or images used have to be imported and hosted somewhere. If it’s a container image then you might host it inside a private registry (e.g. Harbor) that has an SSL certificate signed by your CA. Without trust for that CA in the Supervisor, you can’t deploy the image.
I had exactly that issue recently and the solution was not immediately easy to find because the VMware documentation didn’t call out this particular use-case. If I had been searching for how to get the Supervisor to use an HTTP proxy server though, I would have found it. It just turns out that the same feature addresses both!
The documentation page in question is this one: Configure the Supervisor to Use a Proxy. Following the instructions contained on the page will enable your Supervisor to make use of an HTTP or HTTPS proxy server. Of course, for an HTTPS proxy server to work, the Supervisor would have to trust the certificate presented by the proxy, so of course there are settings for handling that.
What’s not clear from the documentation though is that if you just set the trusted TLS certificate and not the proxy settings, then the Supervisor will be able to pull images from a private container registry!
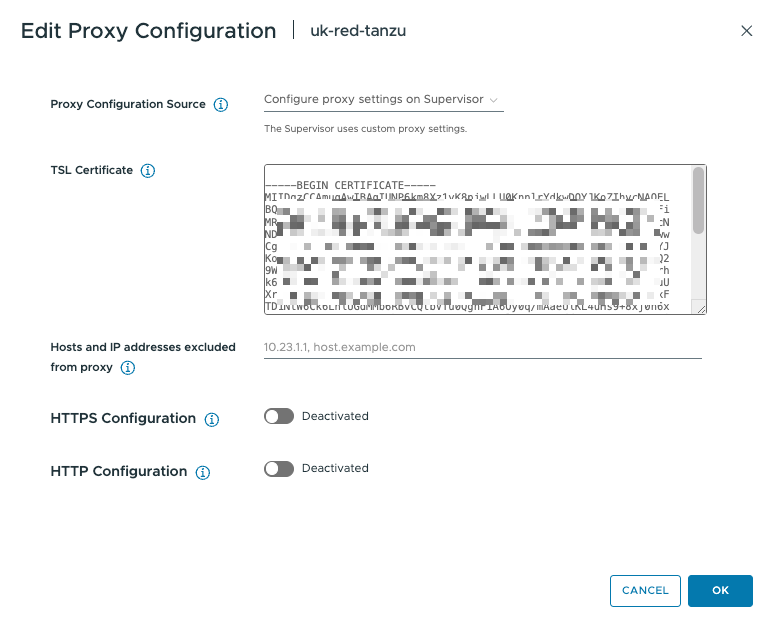
Making the settings as shown above in Figure 1 and saving them triggers a rolling update of the Supervisor. After that completes, my Root CA (whose public certificate I used) is now trusted, as are any service certificates that it has issued, including my Harbor registry.
The one caveat with this, it requires VMware vCenter 8.0.3 and the Supervisor must be at 1.28 or greater.
